We finally have an official response from CISA to the sealed report drafted by Univ. of Michigan computer science expert J. Alex Halderman. The 96 page report allegedly shows numerous vulnerabilities in the Dominion Democracy Suite ImageCast X (ICX) ballot marking devices (BMDs). To much scrutiny, it was sealed by Federal Judge Amy Totenberg in the Curling v. Raffensperger case that has been on going since 2019.
Upon initial analysis of the technical aspects of the advisory, it’s essentially Greek to me. However, the “mitigations” listed at the bottom of the advisory suggest the statement that “CISA has no evidence that these vulnerabilities have been exploited in any election” is based on little, if any, investigation into what actually happened in the 2020 election in the state of Georgia.
In this article, we will deal with each applicable mitigation bullet point CISA makes individually:
- Contact Dominion Voting Systems to determine which software and/or firmware updates need to be applied. Dominion Voting Systems reports to CISA that the above vulnerabilities have been addressed in subsequent software versions.
This recommendation drew scrutiny from Halderman himself in the AP article when Halderman said “no one but Dominion has had the opportunity to assess their asserted fixes.” We have all hopefully heard of the “trusted build” that was installed in Mesa, CO, resulting in the subsequent arrest of clerk Tina Peters for dutifully making a back up copy of the system prior to the update (standard accounting procedure in ANY industry, especially when there is a federal law mandating their preservation). In that “Trusted Build,” it is alleged that tens of thousands of files were erroneously deleted. And because CO Sec. of State Jena Griswold has passed a “law” forbidding third party audits of the elections, we may never know the significance of those files “officially”.
That hasn’t stopped patriots like Ashe Epps, Holly Kasun and Shawn Smith from investigating this further and orchestrating at least three reports on the Mesa, CO findings. They are shocking.
-Ensure compliance with chain of custody procedures throughout the election cycle.
One of the investigators I’ve been working with on all of this in the state of Georgia once told me “election records in Fulton Co and neighboring counties are so bad that it has to be deliberate.” Why would he say something like that? Because election records are beyond disheveled. I am talking epic malfeasance. Original ballot images destroyed. No signatures on poll closing tapes. No zero tapes provided from open records requests. Access by private parties on their own personal laptops to the E-Net system in Georgia (election registration database). Ballot drop box transfer forms missing, forged or illegally duplicated.
If a paper trail and chain of custody records is the “safety procedures” that are meant to reduce the risk of these exploitations, well, we have a major problem in the state of Georgia because the paper trail is practically non-existent.
- Ensure that ImageCast X and the Election Management System (EMS) are not connected to any external (i.e., Internet accessible) networks.
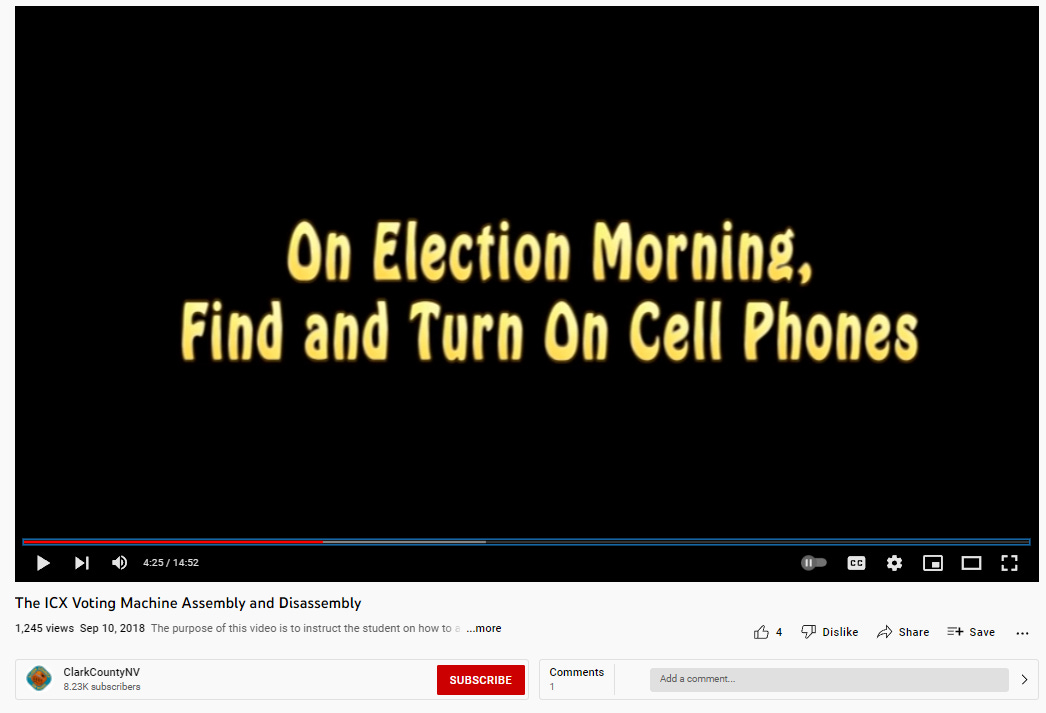
I do not know whether or not the ImageCast X machines in Georgia connected to the internet. I have reason to believe they do. However, it is worth noting that this is the official YouTube channel of Clark Co, NV and this is their official “set up” video for the Dominion ICX machines. At the 4:20 mark, the screen reads “On Election Morning, Find and Turn On Cell Phones” and the narrator says “Find the cell phones inside the same storage box as the kiosks. They are stored inside a plastic shoe box. Turn the cell phones on IMMEDIATELY.”
-Use separate, unique passcodes for each poll worker card.
This one is more difficult to prove in Fulton and other GA counties because there hasn’t been any in-depth analysis or audit and the system log files in Fulton were apparently deleted.
However, if you remember back to the Maricopa Audit, the auditors claimed that the passwords for administrators all used the same login and the same password. This phenomenon of mirrored passwords and logins seems to be a reoccurring theme with similar discrepancies discovered in Pennsylvania, Michigan, and Wisconsin.
-Ensure all ImageCast X devices are subjected to rigorous pre- and post-election testing.
At best, Logic and Accuracy testing, which is statutorily mandated to be conducted prior to elections with notice given to the public to observe, took place on only a small fraction of the machines. According to my interview with Bridget Thorne, the L&A testing was not properly conducted as only the scanners were each tested. The ICX BMDs that are mentioned in this report were *not* tested individually.
Furthermore, there is evidence received from Fulton Co. that none of the machines were tested prior to in-person voting. Gabriel Sterling, COO of the Ga SoS’s office, whom was a private contractor not subject to open records request during the election, claimed that the county ordered 1.1 million mail-in/emergency provisional ballots because they weren’t sure the L&A testing would be completed on time due to a “de minimis” software update done days before in-person voting began. He wanted to ensure that there was a method voters could vote if the machines couldn’t be used. Fortunately, these machines can apparently be used safely without any testing, none the less “rigorous” testing.
Citizen journalist/investigator Kevin Moncla has covered this extensively. I cannot recommend enough reading this article to understand how thorough the L&A testing has been gone through to ensure that we are making accurate statements.
-As recommended by Dominion Voting Systems, use the supplemental method to validate hashes on applications, audit log exports, and application exports.
Once again, my last article dealt with a fact check that showed Christina Bobb of OANN was correct when she asserted that Fulton Co is missing 17,690 ballot images from the original scan. She is correct in more ways than one: the 17,690 that she mentions are missing are, in fact, missing from the recount scan. Gone. Don’t exist. No records found. They also counted 3,125 duplicates in the recount tallies (see for yourself!). Oh, and all of the original ballot images are completely gone. Deleted. All but the absentees.
But more importantly than the missing ballot images are the .sha files. A .sha file is a hash validation file that is created with each and every ballot image that the Dominion system creates. It is a hash validation that would allow you to ensure that the ballot image file itself has not in any way been altered or replaced, otherwise it would return a different hash value.
This is incredibly significant because we are dealing with a vulnerability that would allow a nefarious user to potentially “…mark ballots inconsistently with voters’ intent, alter recorded votes or even identify voters’ secret ballots,” according to the report’s author, J Alex Halderman. So when the election officials in Fulton Co. claim that they have the ballot images, they do. But they are not the originals. They were created during the machine recount of the ballots. And without the original scans or, more importantly, the .sha files to validate their authenticity, it is impossible to know if the ballot images are representative of the voter’s original intent or if they succumbed to the vulnerabilities anticipated to be mentioned in the report.
For more on the .sha files, once again please check out this article by Kevin Moncla.
-Encourage voters to verify the human-readable votes on printout.
As part of Halderman’s contributions to Curling v. Raffensperger, he has authored a brief in which he makes several assertions relevant to human’s verifying their printout:
1. Voters cannot read the QR codes, but they are the only part of the ballots that the scanners count. My report details several routes by which malicious hardware or software can manipulate the QR codes and cause the recorded votes to differ from voters’ selections.
2. In addition to the barcode-only attacks I just discussed, my report demonstrates that Georgia’s BMDs can be manipulated so that both the barcodes and the printed text indicate the same fraudulent selections.
3. The only reliable way to detect it would be if enough voters carefully reviewed their ballots, noticed that one or more selections differed from their intent, and reported the problems to election officials, and if Georgia officials then discerned from the pattern of voter reports that the BMDs were systematically misbehaving.
It should be evident why the initial ballot images and the SHA-256 validation files that are to be provided by Dominion as per their contract are essential to ensuring these vulnerabilities were not exploited.
But CannCon, there was a hand recount! Yes, there was. And it was highly scrutinized by many experts and officials, including Philip Stark, who invented the Risk-Limiting Audit, and Georgia Governor Brian Kemp.
Philip Stark’s declaration regarding the “audit” conducted in Georgia is absolutely devastating to the “no evidence vulnerabilities were exploited” argument considering he outlines that no one actually looked or checked. His explanation begins on pg 6 at number 23 titled “The 2020 ‘Audit’”.
Below is the official letter sent by Gov. Brian Kemp on Nov 17, 2021. In it, he states there are “36 inconsistencies” that are “factual in nature, pose no underlying theories outside of the reported data, and could not be explained by [his] office after a thorough review detailed below.”
-Conduct rigorous post-election tabulation audits of the human-readable portions of physical ballots and paper records, to include reviewing ballot chain of custody and conducting voter/ballot reconciliation procedures. These activities are especially crucial to detect attacks where the listed vulnerabilities are exploited such that a barcode is manipulated to be tabulated inconsistently with the human-readable portion of the paper ballot
This last one somewhat summarizes what we’ve already explained, essentially: the Georgia 2020 election was riddled with glaring inconsistencies, negligent disregard for election procedures and a uniform inability to keep and maintain election records.
It is mind blowing how any one could possibly make the claim there is “no evidence” these vulnerabilities were exploited given the following:
-the “de minimis” software update just days before in person voting began
-the subsequent phantom Logic and Accuracy Testing with no public notice or observation
-Dominion running the above alluded to “testing” due to a convenient COVID outbreak in the English St warehouse
-Stacy Abrams’ affiliated Happy Faces contracting to run the 2020 election and run-off
-Logic and Accuracy skipped on all of the ICX BMDs (in question in this report)
-Missing ballot drop box chain of custody forms
-Missing ballot drop box CCTV footage
-Missing zero tapes from opening the polls (9 out of 500 provided)
-Missing signatures, as required by law, on almost all of the Poll Closing tapes
-Missing ballot images and validation files from the original ballot scan
- In person votes that magically seem to just appear
Anyone who reads this and can put aside partisanship will absolutely question the integrity of our elections. They should be furious that we are being gaslit by elected officials and mainstream media conglomerates to believe this was the ‘safest most secure election in our history’. It was everything but that. And they will censor us until we disappear or they skate to their 22-month retention deadline in September.
Let CISA know that we do not appreciate being lied to and being told there is “no evidence” these vulnerabilities were exploited. Ask them what they examined to draw this conclusion.
Email: CISAservicedesk@cisa.dhs.gov
Toll Free: 1-888-282-0870




Dang Brian!!! Awesome work. You know this stuff better than anyone else I follow and you do an excellent job of presenting it!!
This was great to look over, thanks for putting all this together!
Regarding the"Greek" - something that you may find helpful. I think understanding these concepts gives a little more dimension to just how vulnerable these systems are in ways you haven't commented on above. Even though these analogies are probably nails on a chalkboard to a real cyber security expert, here's my stab at it.
2.2.1. IMPROPER VERIFICATION OF CRYPTOGRAPHIC SIGNATURE CWE-347
"does not validate application signatures to a trusted root certificate"
Let's say you bought a ticket at a concert. You show up, show your ticket, and the gatekeeper lets you in.
The guy just behind you says "hey, sorry, I don't have a ticket, but here's a piece of paper where I wrote down the time and amount I paid, and my seat." The gatekeeper lets him in, too.
Then the next guy passing down the street overhears that, changes course, pulls a piece of paper out of his pocket, writes some stuff down, and uses the same excuse to get into the concert. The gatekeeper just lets him through.
At this point, you may wonder why you bothered to print out the ticket in the first place when you could just write up your own on a crumpled up piece of paper.
Each attendee is a process (software) that needs to make sure it gets approval to do what it's doing by the root (gatekeeper). Not every single action it does after getting in can be monitored, so the system assumes it should be OK as long as it has a valid cryptographic key (the ticket.) When this ticket isn't checked against a verifiable standard .... well ...
2.2.2 MUTABLE ATTESTATION OR MEASUREMENT REPORTING DATA CWE-1283
Your car isn't starting, so you take it to the shop. They first check the blinker fluid, then the tire pressure, then the gas tank. They give you a report, charge you a bunch of money, and give you your keys back. Would you trust that they know how an engine *should* start up? How would you measure their competence? What if they just assured you they knew what they were doing, and you didn't know what you were talking about?
Both the "should" and the "measurement" are accomplished by creating a one-way hash as the computer system starts up. The central processor does this by going through a checklist at startup, computing the hash value, and storing it permanently (cannot be rewritten.) This issue means one, two, or all three of those steps are not happening.
2.2.3 HIDDEN FUNCTIONALITY CWE-912
"ImageCast X has a Terminal Emulator application"
Oh boy, this is a good one. Since we're talking about cars, let's stick with that one. Let's say you got a Tesla. You want to open up the hood on that thing up and start soldering connections? Probably not, you just want to drive it and let the experts get under the hood. You know you could do more damage than good if you go under the hood.
In fact, Tesla probably won't even let you get under the hood because they know you'll screw it up. So you can't get access to certain parts of the car without very specific tools that are only accessible by their approved technicians.
You know what that terminal application is they talk about? Yeah, it's a multi-function tool that let's anybody get under the hood.
2.2.4 IMPROPER PROTECTION OF ALTERNATE PATH CWE-424
"ImageCast X allows for rebooting into Android Safe Mode, which allows an attacker to directly access the operating system"
When you wake up one morning and your back is out, you go to the doctor to figure out how to re-align it. That means you get laid out in a vulnerable position while he works on you (chiropractor), images you (x-ray), or drugs you (surgery). One way or the other, that is not your normal state - you're only in that state to be directly influenced under the practitioner's control, assuming he knows what's best.
Safe Mode is a mode on a computer that allows an administrator (hence reference to "escalated privileges") to debug something that went wrong. Maybe the memory needs a check run, maybe registers need to be edited, maybe standard security needs to be disabled to find the problem. In any case, if that mode is exposed to an attacker, it is all too easy to put a twist in the computer's normal function.
2.2.5 PATH TRAVERSAL: '../FILEDIR' CWE-24
"cause arbitrary code execution by specially crafted election definition files"
Let's say you're asking me for travel advice in Germany, and I tell you the very best thing to do is to coddiwomple Bavaria- everything else is a side-show. You don't happen to know what "coddiwomple" means, and I never explained myself, so you go look it up on Wikipedia.
Unbeknownst to you, the definition of that word in Wikipedia just changed between when I used the word, and when you looked it up. Instead of what I meant - to go with certainty in an uncertain direction - now Wikipedia says otherwise - to throw oneself off a cliff.
Having the ability to change definitions on the fly like that is a problem. Suddenly what the system thinks it should be pointing to changes fundamentally - so there's no consistent way to evaluate what went wrong unless you captured the definition in that particular moment.
2.2.6 EXECUTION WITH UNNECESSARY PRIVILEGES CWE-250
Let's go back to an auto example. Let's say you took your Tesla in to get worked on, expecting a mechanic to work on it. After you give the keys away, you happen to look through the window and notice the mechanic left your car for a moment.
A random guy off the street walks up to your car, looks inside, grabs some spare clothing and tools that make him look like a mechanic, and starts digging around under the hood of your Tesla. The real mechanic comes out, sees someone else is working on your car, and walks away, thinking someone else is handling it.
You turn around and ask "hey, does that guy work for you? Is he a mechanic?" The guy in the office looks up, sees a guy in mechanic's clothes, and says "well, I don't know him personally, but he probably works for us."
Does that seem like a normal situation? No, because you watched it happen, and everyone else just assumed he had the right privileges because he was wearing the clothes.
That's what this means about the ability to allow a random software to a "system level service." System level should be maintenance only, and will be allowed to do more things "under the hood" than a regular application should be able to do.
Lastly, I think the last three are pretty self-explanatory.
2.2.7 AUTHENTICATION BYPASS BY SPOOFING CWE-290
2.2.8 INCORRECT PRIVILEGE ASSIGNMENT CWE-266
2.2.9 ORIGIN VALIDATION ERROR CWE-346